-1920x1215.jpg)
Azure MFA - "Number Matching"
"Number Matching" will be activated by default as of February 27, 2023
Number Matching (MFA Number Matching) is an important security improvement over the traditional second factor notifications in Microsoft Authenticator. Microsoft will remove admin controls and enable number matching for all users globally starting February 27, 2023.
Why number matching (MFA Number Matching)?
The main reason for enabling number matching is to increase the security of the Microsoft Authenticator application. There are many articles about MFA fatigue attacks. By implementing number matching, users can be prevented from accidentally approving MFA requests. With number matching, the user has a context for the MFA request to make better decisions. If they do not have the number lookup on their computer, the MFA request cannot be approved.
What changes?
We can enable number matching for our users today, we don't have to wait for Microsoft to release it. In its current state, number matching can be enabled for all Microsoft Authenticator users or for a selected group of Microsoft Authenticator users. Let's take a look at these settings in the Azure portal(https://portal.azure.com)
Open the Azure Active Directory in the Azure portal. Select Security in the left menu. In the next windows, select Authentication methods and then Policies. Microsoft Authenticator policies can be configured here. This section defines which of your users are allowed to use the Microsoft Authenticator application and the settings for number matching (MFA Number Matching) can also be configured.
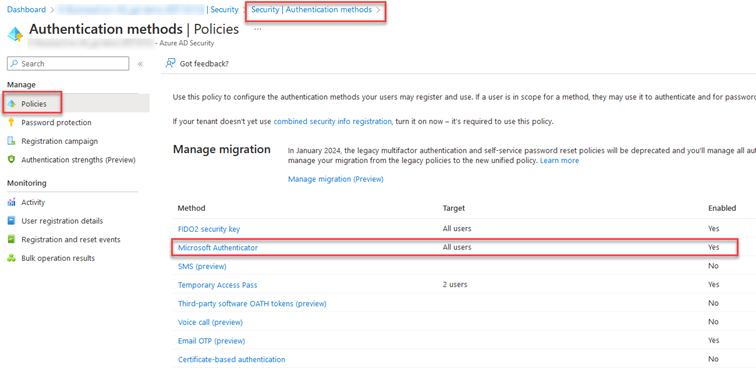
After selecting the "Microsoft Authenticator" item, the following window is displayed:
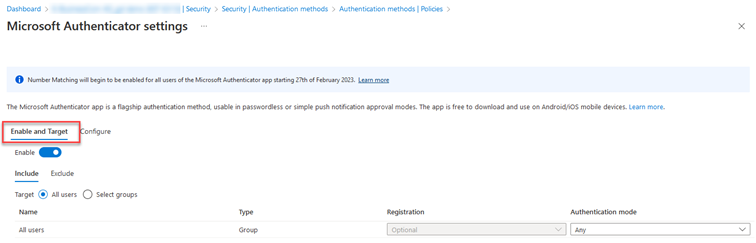
On the Enable and Target tab, you can configure which users are allowed to use the Microsoft Authenticator application as an authentication method. In my case, I have configured "All users" with any authentication mode. The two available modes are Passwordless and Push. You can still make changes to these settings after February 27, 2023.
You can address specific users or groups and add exceptions if required. For example, I can select all users and add an exclusion for some user groups.
On the "Configure" tab, you will find the settings for number matching, as shown in the image below.
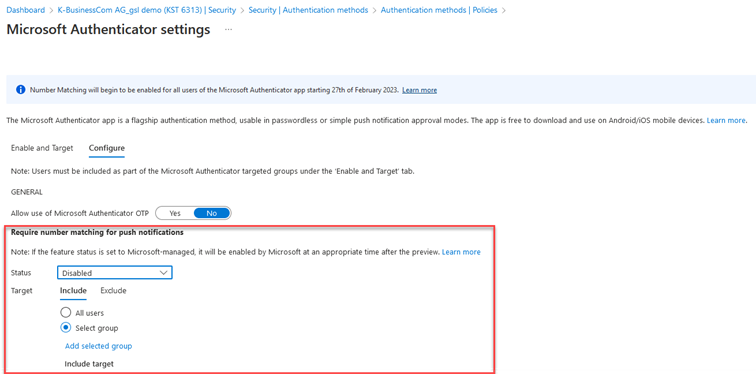
At the moment, these settings, which are shown in the illustration above, can still be changed as required. You can configure these settings to enable MFA Number Matching for all users of the Authenticator application or to target specific users or groups. This is a good way to test this feature on some POC users and familiarize yourself with the new process.
After February 27, 2023, you will no longer be able to change these settings. The Status setting will be set to Enabled. The Target section will be set to All users. As already mentioned, these settings can no longer be changed after this date. You can also not add any exceptions in the Destination setting.
All details on the configuration can also be found in the Microsoft documentation.
Which users are affected?
The changes only affect users of the Microsoft Authenticator application. Users of other authentication methods such as phone (SMS/text) are not affected.
Microsoft will not force all users to use number matching by default. Number matching will only be enabled by default for users of the Microsoft Authenticator application.
New users can continue to sign in using any authentication method according to the policy you have configured. If they sign in for phone authentication, they continue as usual. If they sign up for Microsoft Authenticator with push notification, they use number matching.
Azure MFA NPS Extension
If you use the Azure MFA NPS Extension to connect 3rd party products such as Citrix Netscaler or your firewall for VPN client access, please check the installed version and update it if necessary.
All details can be found here and a short test of how this works with Citrix can be found in this article.
If you have any questions, please contact our specialists.